- Automated code reviews for newly created merge requests
- AI-powered suggestions displayed directly on merge requests
- Interactive assistance through the CodeRabbit bot for real-time feedback
- Seamless integration with your existing GitLab workflow
Using self-hosted GitLab? See our Self-managed
GitLab integration guide for on-premises
installations.
GitLab Access Tokens
To enable CodeRabbit to interact with your GitLab repositories, you need to provide an access token that grants the necessary permissions for the Merge Requests and Discussions APIs. Choose the token type that best fits your organization’s needs:Personal Access Token
Create a dedicated service account for CodeRabbit with a personal access
token
Group Access Token
Use GitLab Premium/Ultimate’s group tokens with automatic bot user creation
Personal Access Token
We recommend creating a new user as a service account, associating this user to the group you’d like to install CodeRabbit on, and providing CodeRabbit with the personal access token to allow access. During the installation process, CodeRabbit will automatically configure the required webhook for seamless integration.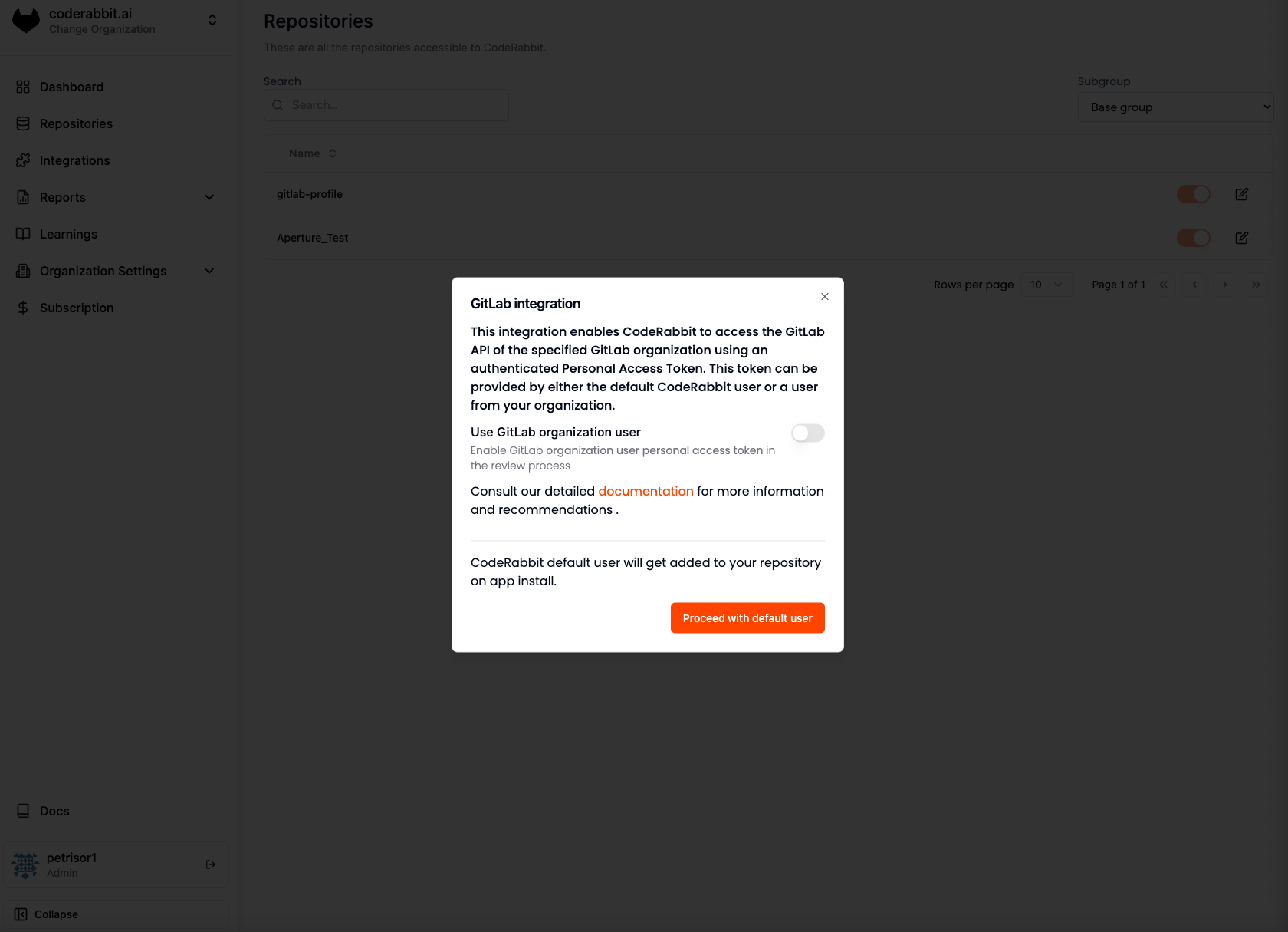
If you wish to change the review user, you must provide the access token for
the new user who will post reviews and comments. However, this requires
manually removing the previous user from the projects and associated webhooks.
Once this is done, you will need to reinstall the CodeRabbit app for each
project.
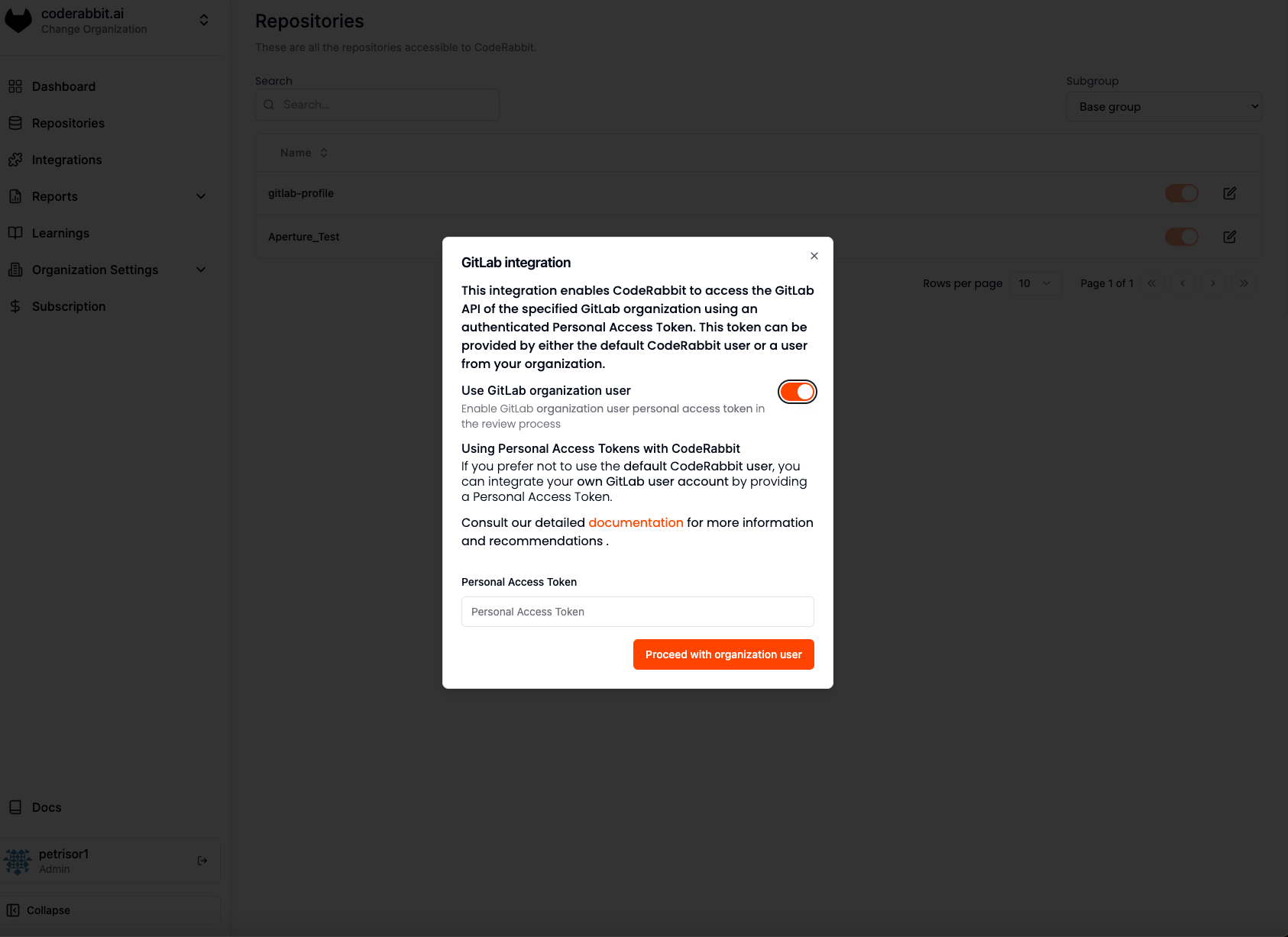
Best Practices for Service Account Setup
Follow these recommendations when setting up your CodeRabbit service account:- Username: Use “CodeRabbit” as the username for easy recognition
- Email: Use a dedicated email address for easy identification and management
- Profile picture: Use the CodeRabbit logo for easy recognition. Download our logo here
- Permissions: Ensure the dedicated user has at least Developer access to the group or projects where you want to install CodeRabbit
Important Considerations
Review Attribution: Code reviews will be attributed to the owner of the
personal access token, so they’ll appear to come from your service account
user.
- Navigate to the GitLab User page in the sidebar
- Enter the new access token and click the Update button
Generating a Personal Access Token
Log in to your CodeRabbit service account
Log in using the user designated for CodeRabbit reviews. This user serves as
a service account for managing reviews and related activities.
Navigate to access tokens
- Select your avatar on the left sidebar 2. Choose Edit Profile 3. Select Access Tokens from the left sidebar 4. Click Add New Token
Configure token settings
- Enter a descriptive name for the token (e.g., “CodeRabbit Integration”)
- Set an expiry date for the token
If no expiry date is entered, it defaults to 365 days from the current
date.
Select required scopes
Ensure the following scopes are selected: -
api - Full API access -
read_api - Read-only API access - read_user - Read user information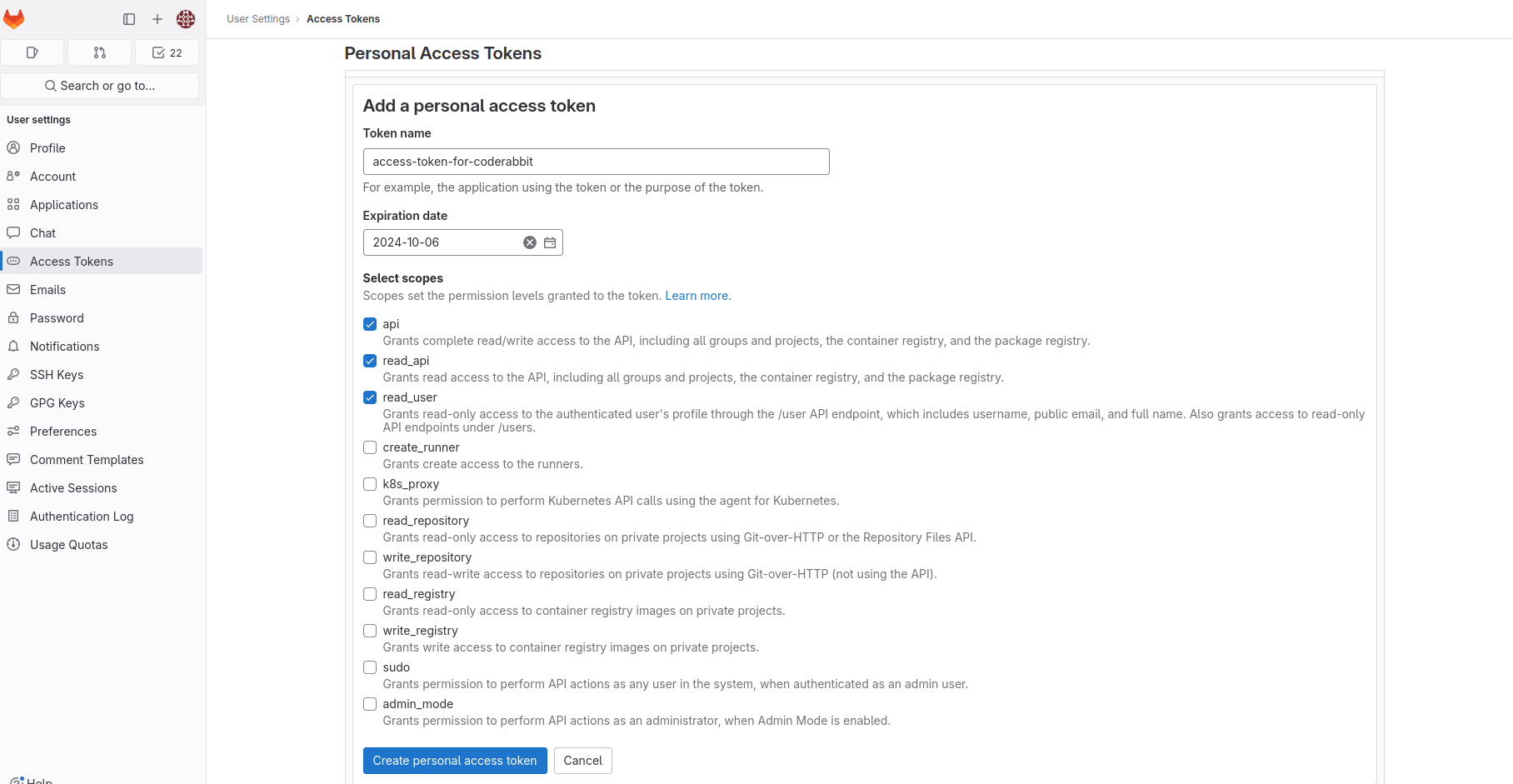
Group Access Token
Creating a Group Access Token in GitLab automatically generates a bot user. Ensure that the token is configured with Developer access. Once set up, you only need to provide this token for integration. Note that a Group Access Token is limited to the scope of the group where it was created. To configure additional groups, you will need to generate a separate Group Access Token for each group.By default, GitLab restricts this option to users on the Premium or Ultimate
tiers.
Generating a Group Access Token
Access token settings
- Select Settings from the left sidebar 2. Select Access Tokens within the Settings heading
Group Access Tokens create bot users with generic GitLab-generated usernames (like
group_63_bot_5753...). If you prefer a more descriptive username for your CodeRabbit bot, you can customize it using the GitLab API.You can find the bot’s user ID through the CodeRabbit UI if connected, or by visiting the bot user’s profile from your Group Members page in GitLab.Configuring Access Tokens in CodeRabbit
GitLab onboarding requirement: The user completing the CodeRabbit onboarding flow must be a GitLab group owner. By default, if no access token is provided, CodeRabbit will prompt you to provide one during the installation process. However, if you wish to provide the token beforehand, you can do so by navigating to the Organization Settings tab, and selecting the GitLab User tab on the sidebar. Once entering the token, the token will be validated and saved for future use. You can confirm the correct user is being selected by verifying the user ID shown on the UI with the user ID of the service account user you created.Repository Installation
Access repository settings
Go to the Repositories
page in the CodeRabbit
app.
Select repositories
Select the checkbox next to the repositories where you want to install
CodeRabbit.
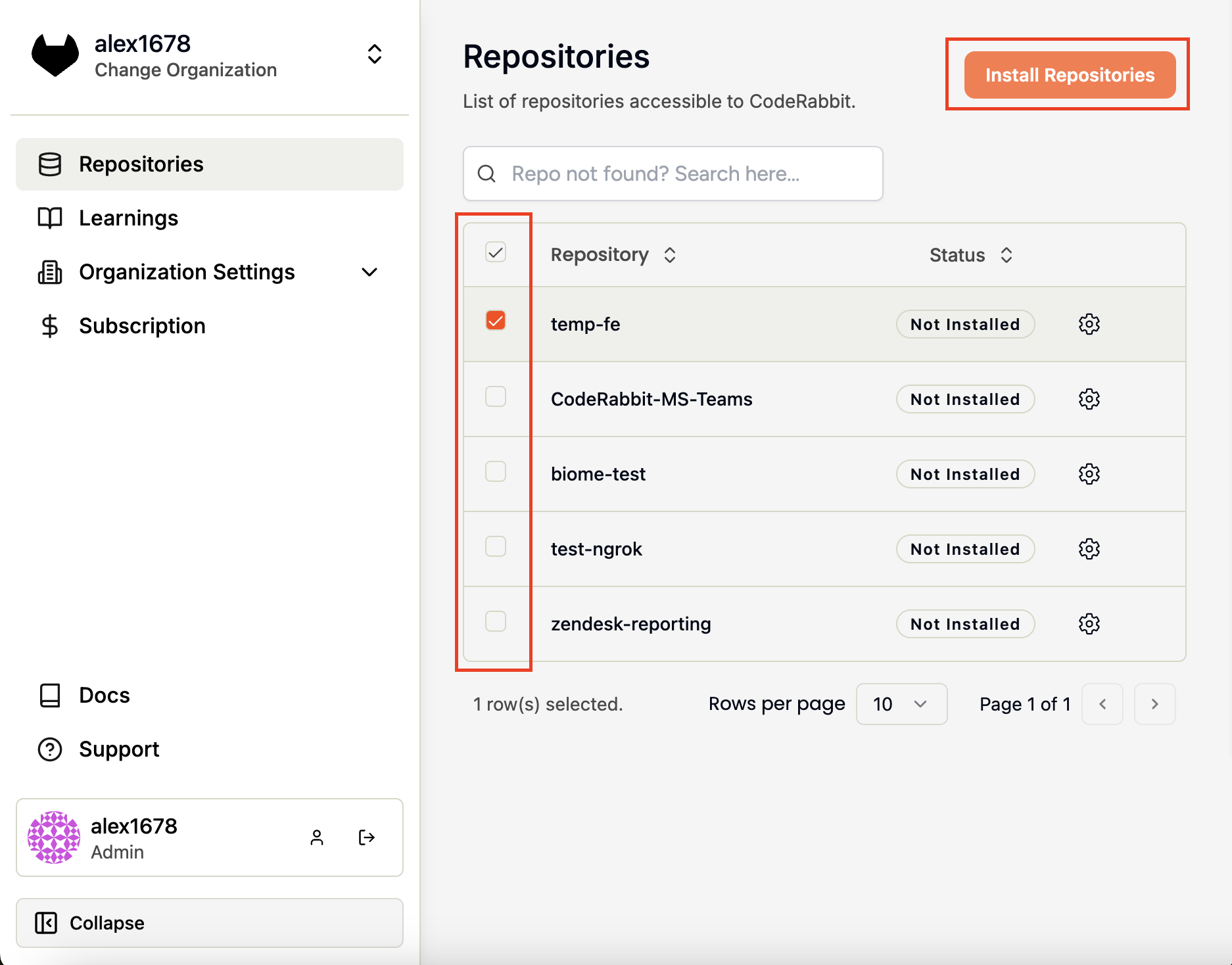
https://coderabbit.ai/gitlabHandler will now be installed for the projects selected.
Troubleshooting
If you are experiencing issues with the webhook, such as CodeRabbit not being able to access the repository, or not reviewing merge requests, you can manually delete the webhook from the repository.Then refresh the repository page in the CodeRabbit app and reinstall the webhook.If you cannot install the webhook, please check that your GitLab user has the necessary permissions to install the webhook and the PAT is not expired.